Entries Tagged 'Rants' ↓
December 13th, 2006 — Rants, Research
Sawsan Salameh has been dreaming of getting a doctorate since the age of sixteen. Now 29, her dream has been placed on hold because none of the universities in her native Palestine offers a Ph.D. program in theoretical chemistry, her chosen subject. Studying abroad wasn’t an option, for she comes from a traditional Muslim family and believes traveling abroad alone is improper. Making matters worse, her father recently passed away, leaving Sawsan to provide for her mother and younger sister.
Suddenly, luck changed for Sawsan. She applied to Hebrew University in East Jerusalem, just a short drive from her home in the West Bank, and not only did she gain acceptance, she received a full scholarship. She hopes to use her future degree to launch a career as a chemistry professor.
Only one obstacle remains: the Israeli checkpoint at the East Jerusalem border. Protected by barbed wire and machine guns, it blocks Sawsan from even setting foot on the university’s campus. Obtaining a permit for entry is possible—fourteen Palestinian students are currently enrolled in Israeli universities—but Sawsan’s application was denied eight times. (The government of Israel has become much tighter with permits since the Hamas takeover of Palestine in March.)
With help from the human rights group Gisha, Sawsan appealed to Israel’s High Court of Justice. After a month of delays and hearings, Sawsan’s dream was finally about to come true! The court overruled the government and approved a permit that would allow her to attend school in Israel…for six months.

Sawsan Salameh
Photograph © BBC News
The idea that anyone could complete a doctoral degree in six months is ludicrous. To put this in perspective, consider that in the United States, earning a Ph.D. in the sciences requires about seven years of post-Bachelor’s study. Sawsan’s six-month permit, which the High Court apparently considers a gift, is as good as none.
The Israeli authorities haven’t commented publicly on this case, so one can only imagine what they were thinking.
September 18th, 2006 — Rants, Software, Tips
Most people know that when you sell or give away a computer, you should format its hard drive to make sure your sensitive information doesn’t fall into the wrong hands. And most of those people know that formatting a drive doesn’t actually erase all the data. Instead, you should use a special utility that overwrites every block of data on the drive. And a smaller portion of those people know that overwriting a block just once isn’t enough. If you really want to be safe, you should apply the Gutmann method, which overwrites every data block 35 times. And an even smaller portion of those people know that the Gutmann method is a myth.
I had always thought that the idea of overwriting the same data block 35 times was a bit dubious. (Why would 35 times be secure but 34 times not be?) And yet, most disk utilities provide an option to erase a hard drive 35 times over.
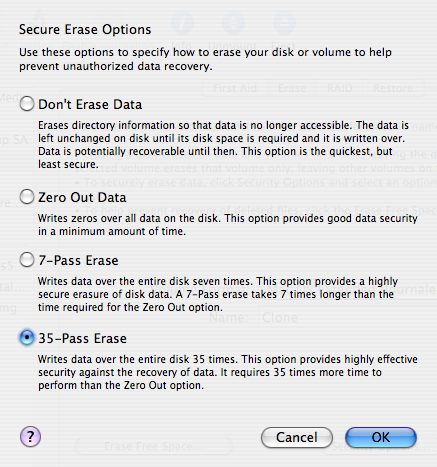
In a recent Slashdot article, I discovered a comment that shed some light on this issue. User Psionicist wrote (with typos faithfully reproduced):
I would like to take the oppertunity here to debunk a very common myth regarding hard drive erasure.
You DO NOT have to overwrite a file 35 times to be “safeâ€. This number originates from a misunderstanding of a paper about secure file erasure, written by Gutmann.
The 35 patterns/passes in the table in the paper are for all different hard disk encodings used in the 90:s. A single drive only use one type of encoding, so the extra passes for another encoding has no effect at all. The 35 passes are maybe useful for drives where the encoding is unknown though.
For new 2000-era drives, simply overwriting with random bytes is sufficient.
Here’s an epilogue by Gutmann for the original paper:
Epilogue In the time since this paper was published, some people have treated the 35-pass overwrite technique described in it more as a kind of voodoo incantation to banish evil spirits than the result of a technical analysis of drive encoding techniques. As a result, they advocate applying the voodoo to PRML and EPRML drives even though it will have no more effect than a simple scrubbing with random data. In fact performing the full 35-pass overwrite is pointless for any drive since it targets a blend of scenarios involving all types of (normally-used) encoding technology, which covers everything back to 30+-year-old MFM methods (if you don’t understand that statement, re-read the paper). If you’re using a drive which uses encoding technology X, you only need to perform the passes specific to X, and you never need to perform all 35 passes. For any modern PRML/EPRML drive, a few passes of random scrubbing is the best you can do. As the paper says, “A good scrubbing with random data will do about as well as can be expectedâ€. This was true in 1996, and is still true now.
Looking at this from the other point of view, with the ever-increasing data density on disk platters and a corresponding reduction in feature size and use of exotic techniques to record data on the medium, it’s unlikely that anything can be recovered from any recent drive except perhaps one or two levels via basic error-cancelling techniques. In particular the the drives in use at the time that this paper was originally written have mostly fallen out of use, so the methods that applied specifically to the older, lower-density technology don’t apply any more. Conversely, with modern high-density drives, even if you’ve got 10KB of sensitive data on a drive and can’t erase it with 100% certainty, the chances of an adversary being able to find the erased traces of that 10KB in 80GB of other erased traces are close to zero.
So it seems my suspicions have been confirmed: You do not need to erase a hard drive 35 times before selling it on eBay. A quick zeroing out of the data is sufficient.
August 17th, 2006 — Mac, Rants, Research, Software
My colleagues and I were finally able to publish our Autonet research at a conference in Chicago. Being the lead author, I hopped on a flight to the Windy City last Tuesday to present the results of our work. When I arrived at the hotel, I met the other two speakers scheduled for the afternoon session. The first one was busy setting up his Dell at the podium while the audience slowly began to fill the room. The second speaker had no laptop, only a USB drive with his slides; he was hoping to borrow the first speaker’s Dell.
We were about two minutes away from showtime when the projection screen suddenly froze. Here’s what everyone in the audience saw:

It turned out that the guy’s Dell was crashing whenever he tried to start his PowerPoint presentation. Rebooting didn’t help. Windows insisted on giving him the Blue Screen of Death.
By this time, we were now late. Frustrated, the two speakers saw me typing on my Mac and asked if I could help. I walked up to the podium, plugged my Mac into the projector, loaded both of their presentations into Keynote, and returned to my seat. The first speaker then began his presentation using my PowerBook. Then the second speaker. Then me.
No BSoD. No crashing. It just worked. My Mac saved the day!
Hmm, that reminds me of an ad…

June 12th, 2006 — Rants, TV
For the last couple of years, Citibank has been promoting its identity theft protection services through a series of TV commercials. The somewhat humorous spots have become quite popular and have even earned Citibank an Emmy award.

Somehow, I’ve always found these commercials slightly annoying. I never knew why; there was just something about them that bothered me. Today I happened to catch the “Thelma and Norma†spot while watching the NBA Finals, and that’s when it hit me: The commercials have it all backwards!
You see, the premise of each commercial is that the person on-screen has had his or her identity stolen. That’s the reason why the characters speak in a voice that doesn’t match their appearance. But wait a minute… That’s not how identity theft works!
If someone steals my identity, they’ve effectively stolen my “voice,†right? In other words, identity theft allows a criminal to speak with the victim’s voice. But Citibank shows the exact opposite: The victims speak with the criminals’ voices, which makes no sense at all. I realize that these commercials are supposed to be funny, but you’d think they’d at least get the concept right.
Oh, well. Now that I know why the commercials always felt wrong to me, maybe I can begin to enjoy them for what they are.
June 6th, 2006 — Rants
The four or five people who read this blog may have been asking themselves why it was unavailable for the last two weeks. Was there a major power outage? Did the web server crash? Did Trevor forget to pay his hosting bills? No. It was all because of a single DMCA take-down notice (more on that later).
It began with a recent post to my blog. I had cut-and-pasted an informative comment Brian D. Foy had made on another blog. The next day I received an email from Mr. Foy, which read, in part:
Can you trim the quoted material please? Taking the whole response oversteps fair use by quite a bit and is a bit rude.
Rude? I went back to look at the post again. Did I insult him somehow? Had I misspelled his name? No, I had given him the proper attribution and linked to both the original post and to two of his websites, which may bring more traffic (and customers!) to him. That doesn’t seem rude to me.
Confused, I replied to his email and told him I thought he was overreacting. After all, I wasn’t copying from a book or article; it was a simple blog comment, only a few paragraphs. Mr. Foy then sent me a reply, which read, in part:
I’m not giving you an implied license to reprint anything. I responded to Erica’s blog and I’d like to keep my reply there. You can excerpt the parts that you like and link to the whole thing, but otherwise I’d like you to respect my copyright now that I’ve made my intent clear.
Okay, so let’s forget about this whole “rude†thing. The real issue here is that Mr. Foy is claiming I have violated copyright law.
Have I? Consider this:
- Look at the bottom of any page in Erica’s blog. It’s licensed under the Creative Commons. What does that mean? It means I have the right to copy, distribute, and modify the page as long as I provide attribution and don’t use it for any commercial purpose. Clearly, my blog is non-commercial, and as I said, I gave full attribution to the source.
- Mr. Foy has acknowledged that Erica’s blog is licensed under the Creative Commons; he’s only asserting copyright to his comment. But this is not possible! When one adds content to a public work that’s distributed under an open documentation license (such as Creative Commons or the GNU FDL), that content automatically falls under the same license. This is common practice on Wikipedia, for example, which is licensed under the GNU FDL. If you add content to Wikipedia, you have no right to claim copyright infringement when someone copies that content (assuming, of course, that the copying complies with the FDL). If Mr. Foy did not want to license his words under the Creative Commons, then he should not have posted them to Erica’s blog.
- The Electronic Frontier Foundation addresses this issue in its Bloggers’ FAQ: “When a person enters comments on a blog for the purpose of public display, he is probably giving an implied license at least for that display and the incidental copying that goes along with it.â€
- Posting a comment to a blog is like sending a letter to the editor of a newspaper. If you write a letter to a newspaper, do you own the copyright to that letter? Can you sue the newspaper for copyright infringement when they publish your letter without permission? I’m not a lawyer, but I doubt any court in the country would allow that. They’d probably say you’re giving the newspaper an implicit copyright to your letter, allowing them to publish it, post it on their website, and so on. And if a third party copies the letter from the newspaper? Well, that’s a gray area, but if anyone were to claim copyright infringement, it would be the newspaper, not the author of the letter. Likewise, I might expect Erica to complain when I copied from her blog, but not Mr. Foy.
Given all of the above, I’m certain I’m not violating anyone’s copyright. Unfortunately, Mr. Foy still didn’t agree, and he immediately shut down my blog! How did he have the power to do that?
It’s all because of a controversial law, passed in 1998, called the Digital Millennium Copyright Act, or DMCA. The law gives copyright holders the right to force potentially infringing material to be removed from the Internet for 10 business days. The two weeks allow them to prepare a lawsuit against the alleged infringer. In other words, the DMCA makes those who post content online “guilty until proven innocent.†Knowing this, Mr. Foy filed a DMCA take-down notice with my hosting provider, who immediately took down my blog.
Well, yesterday was the 10th day, and My. Foy never bothered to sue me. His DMCA take-down notice seems to have been nothing more than saber-rattling. Apparently my copyright violation, if one exists, is not important enough to pursue, which is exactly what I was trying to tell him in the first place. He ended up wasting his time and mine.
And I never did find out why Mr. Foy thought I was being rude or why he was so determined to prevent his blog comment from being copied. Perhaps I would have been more likely to comply with his request if he had simply explained himself. Maybe he posted the comment by mistake, or maybe he was planning to publish the comment in a magazine article. Instead, he simply called me rude and insisted that I meet his demands. Naturally, I wasn’t very receptive.
On the bright side, I got a DMCA take-down notice and a potential lawsuit about a week after I started my blog. That’s gotta be a record, right?
May 9th, 2006 — Humor, Rants
I get a lot of email from people asking for help getting on the Internet with their Treo 650. One such email came to my inbox today, but attached to the bottom of it was yet another one of those stupid email disclaimers. Email disclaimers are wrong for so many reasons, but this one took the cake:
this e-mail contains intelectual property & confidential information belonging to the sender/reciever, which is protected by the physician/patient privilege & WIPO laws and treaties. this information is intended only for the use of the individual(s) named above. if you are not the intended recipient, you are here by notified that any disclosure, copying, distribution, utilization or the taking of any action in reliance on the contents of this information is prosecutable by law. members of medical management office solutions, llc maintains the legal right to protect its concepts, ideas and utilization, implementation of such concepts and ideas as enforceable by law. if you have received this transmission in error, please notify the sender immediately.
Normally when I get a disclaimer like this, as a matter of principle, I simply reply to the sender and tell them that I refuse to help them unless they can correspond with me minus the pointless legal mumbo jumbo. After all, why should I help someone who’s making legal threats against me and might take me to court should I allow their “confidential†email fall into the wrong hands?
But when I noticed that the author of this intellectual-sounding disclaimer misspelled “intellectual,†I just had to respond with a disclaimer of my own. At the bottom of my reply to him, I added the following text:
Unless you are named “Arnold P. Fasnock,†you may read only the odd-numbered words (every other word beginning with the first) of the message above. If you have violated this notice, you hereby owe the sender, Trevor Harmon, $10 for each even-numbered word you have read.
That felt good.




